MuLogin Browser SSL Fingerprint
You can set the number and order of cipher suites in SSL fingerprint setting, which can withstand some websites that use the JA3 method to detect SSL fingerprints. Generally, each browser has a relatively fixed SSL fingerprint. When doing multi-account or anti-detection projects, the change of the SSL fingerprint may play a certain role. However, if you do not know much about what is SSL fingerprint, it is recommended not to set it randomly, otherwise it may be counterproductive.
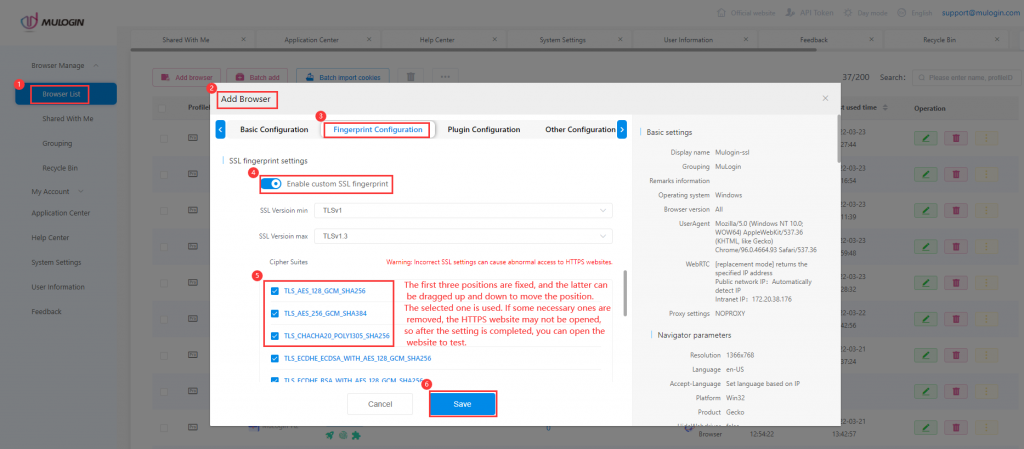
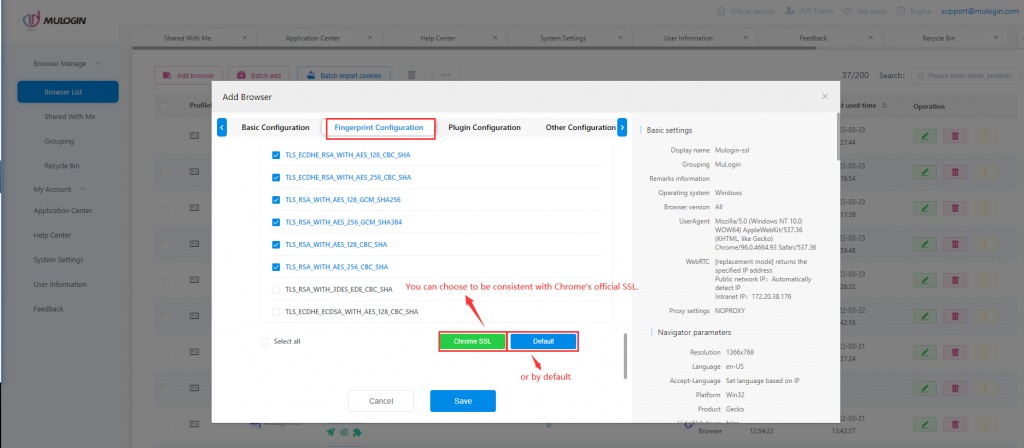
JA3 is a method for creating SSL/TLS client fingerprints that should be easy to generate on any platforms and can be shared easily for Threat Intelligence.
What is SSL fingerprint? Genarally, it can be said that each browser has a fixed SSL fingerprint.
The JA3 method is to gather the decimal values of the bytes for the following fields in the Server Hello packet: Version, Accepted Cipher, and List of Extensions, Elliptic Curves, and Elliptic Curve Formats. Using a “,” to delimit each field and a “-” to delimit each value in each field, then concatenates those values together in order.
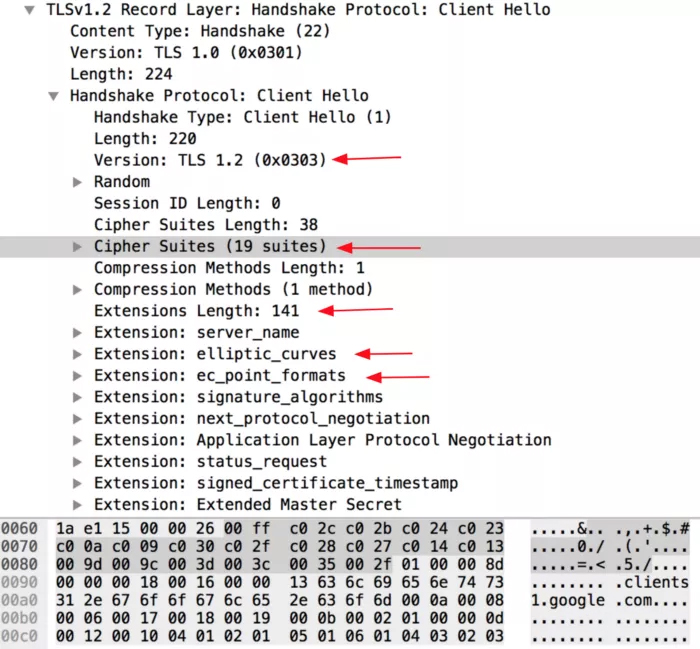
Example Client Hello packet as viewed in Wireshark
The field order is as follows:
TLSVersion,Ciphers,Extensions,EllipticCurves,EllipticCurvePointFormats.
Example:
769,47–53–5–10–49161–49162–49171–49172–50–56–19–4,0–10–11,23–24–25,0
If there are no TLS Extensions in the Client Hello, the fields are left empty.
769,4–5–10–9–100–98–3–6–19–18–99,,,
These strings are then MD5 hashed to produce an easily consumable and shareable 32 character fingerprint. This is the JA3 TLS Client Fingerprint.
769,47–53–5–10–49161–49162–49171–49172–50–56–19–4,0–10–11,23–24–25,0 → ada70206e40642a3e4461f35503241d5
769,4–5–10–9–100–98–3–6–19–18–99,,, → de350869b8c85de67a350c8d186f11e6
We also needed to introduce some code to account for Google’s GREASE (Generate Random Extensions And Sustain Extensibility) as described here. Google uses this as a mechanism to prevent extensibility failures in the TLS ecosystem. JA3 ignores these values completely to ensure that programs utilizing GREASE can still be identified with a single JA3 hash.
Websites that can be used for SSL fingerprinting tests: https://browserleaks.com/ssl
Conclusion
JA3 and JA3S are security analysis methods based on TLS fingerprints. The JA3 fingerprints can identify the way how the client application communicates over TLS and the JA3S fingerprints can identify the server response. If combine these 2 methods, they essentially create a fingerprint of the cryptographic negotiation between client and server. While TLS-based detection methods are not always a silver bullet or a guaranteed mapping to client applications, they are always valuable as a pivot point for analysis.
MuLogin designs the SSL custom setting method, mainly to change the JA3 fingerprint of the browser. Althoufh it is not comprehensive, it is very simple and efficient. Hope to help some users who pursue perfectionism. At the same time, hope users provide us good suggestions and help.